Threat Alert! New NotPetya Ransomware spreading worldwide
Please note, the following article is based on developing information and will be updated as more accurate data is made available by the security community who continues to analyze the threat.
This morning, a new ransomware called NotPetya spread rapidly through government, major corporations, and critical infrastructure in Ukraine, Britain, and Spain. The situation is still developing, but the Ukraine government and a number of major corporations have already confirmed on Twitter that they have been hit and taken offline. (Originally during the initial attack, analysts believed this was a new variant of the Petya ransomware. Upon further review they realized this was something new, so the name has been changed to NotPetya.)
Very early malware analysis indicates that this ransomware is spreading at least in part using the EternalBlue MS17-010 SMBv1 vulnerability used by WannaCry. The ransomware then spreads laterally through the organization using WMIC and PSEXEC, techniques that are very difficult to detect and prevent.
While unconfirmed, it is believed that organizations who have kept up on patches from Microsoft should be inoculated from this attack. However, if some machines in the organization are not patched and become infected, there have been reports that the ransomware can spread even to infected machines by gaining control of credentials or a Domain Controller that grants them access to other machines through legitimate user accounts.
North Sky clients can rest assured that all managed devices have been patched for these vulnerabilities which significantly mitigates the risk of an infection. However, if there are devices in the environment which are unmanaged, such as personal devices used for work purposes, these could become a source of compromise in the environment. We also ensure that services such as SMB are properly firewalled and protected from the outside internet, significantly limiting your exposure.
As part of our ongoing service to you, we regularly review your environment to ensure that all critical data is backed up such that in the event of a worst case scenario like a widespread ransomware infection in your environment, we can effectively get you back up and running in a reasonable turnaround time.
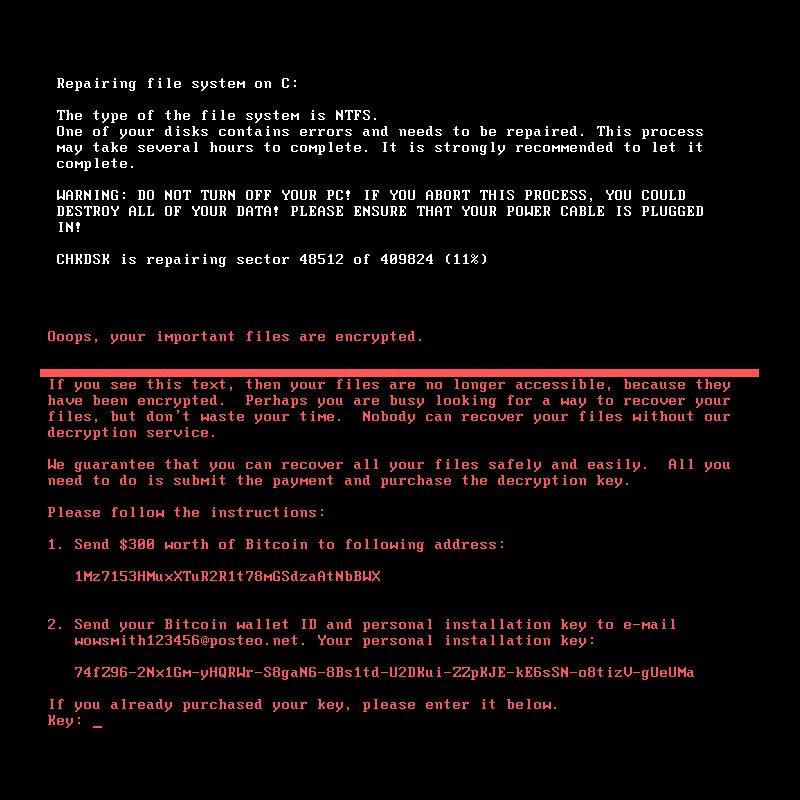
In the event that you notice odd behavior with your computer or see a screen resembling the image in this article, please unplug your computer from power and network immediately and call us at 612-424-2063.
Update 1:23pm CST
Please be aware that it has been reported that the email provider of the attacker has closed the attacker's email account. This means that even if victims pay the ransom, and even if the attacker was willing to provide the decryption keys, there is no way to contact the attacker to get the decryption keys.
Update 4:35pm CST
Analysts have reported that proper patching of systems generally defends against the attack, however there are still risks to patched machines if there are unpatched or infected machines also in the environment. Be sure you're up to date with the latest Windows Updates!
Update 5:55pm CST
If the NotPetya screen pictured above appears on your computer, pull power from the computer entirely. If it is a laptop, you will need to both unplug from AC and remove the battery. This will at least stop the progress of the disk encryption until a Incident Responder can work on the system.
Update 5:58pm CST
For IT experts: there are credible reports that blocking C:\Windows\perfc.dll and C:\Windows\perfc.dat from writing or executing stops NotPetya on patched system. Create the file C:\Windows\perfc (no file extension) to block execution of the malware. If you have a system that is not patched for MS17-010, it is still vulnerable. It is also probably only a matter of time before a NotPetya variant is released that randomizes this filename and works around this fix.
Final Update June 29th, 2017 12:10pm CST
The NotPetya / Petya / NyetPetya / PetyaWrap / Petya.2017 malware has appeared to have been contained from further widespread infection, and the vast majority of AV vendors have updated their signatures to detect and eradicate the infection. For additional post-mortem details, please see the following resources:
For a great, semi-technical breakdown of the event and an excellent summary of why the techniques used caused alarm within the information security community:
Why NotPetya Kept Me Awake (& You Should Worry Too)
For a more deep dive technical analysis: Petya Ransomware Without The Fluff