2 Factor Authentication: What is it and how to use it
Traditionally, access to computers, websites, and systems have been dependent on two things: a username and a password. The username identifies who you are, while the password authenticates that you are who you say you are.
As past articles have discussed, this places a massive security burden on a single factor, your password. Even with the strongest passwords, they can be stolen, guessed, or cracked through no fault of your own. Passwords alone as a single factor of authentication are better than nothing, but there is still a risk exposure. Anyone who gets ahold of that password can fraudulently authenticate themselves as you until you change it or realize what’s happened.
To mitigate this risk exposure, more and more systems are adding the ability to enable 2 Factor Authentication. 2 Factor Authentication (also referred to as 2FA, 2-Step Verification, Multi-Factor Authentication, MFA, or Enhanced Sign-On) is an authentication system that employs two or more of the following to authenticate users:
- Knowledge factor: Something you know. (This is what a password is.)
- Inherence factor: Something you are. (Biometrics such as fingerprints, retinal eye scans, and face scans.)
- Possession factor: Something you have. (Physical items such as phones, security tokens, and ID badges.)
By employing two (or more) of these, now if someone steals your password they still can’t get into your account unless they also compromise your second factor. This makes things much more difficult on an attacker. Passwords can be exposed by hacking systems, recording your keystrokes, or tricking you into entering it into a malicious fake website - but also stealing your fingerprint proves to be much more challenging!
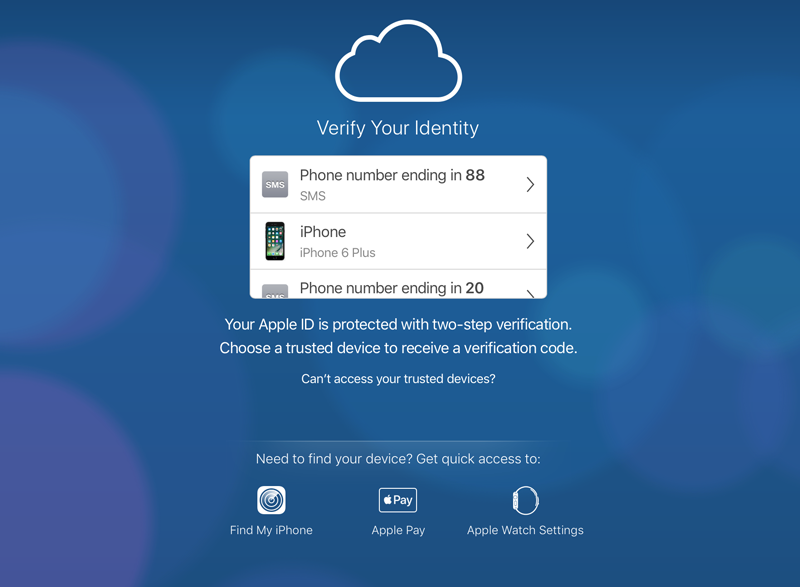
Logging in with 2FA
Most systems today use a Possession Factor as the 2nd factor, something you have. Here’s how a common 2nd possession factor login process works:
- Go to the login page.
- Enter your username and password like normal.
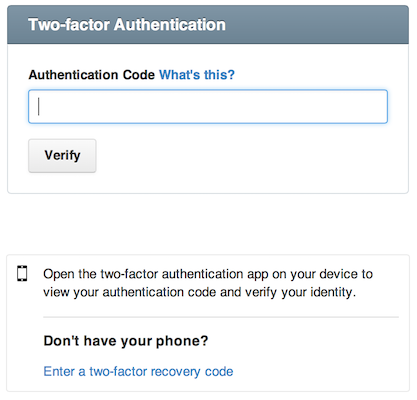
- After correctly entering your username and password, the website will ask you for an Authentication Code, which may also be referred to as a Verification Code, Token, or One-Time Password (OTP).
- You get the token from a different device in your possession, such as a phone or a security key, and enter it into the field.
- Assuming the token is correct, your login is accepted.
Note: instead of a numeric tokens, some systems will prompt you for a fingerprint or face scan as a 2nd factor.
How does this make us more secure?
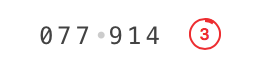 Two things are special about the tokens. First, the tokens are temporal, meaning they change all the time (usually every 30 seconds or less). If someone steals your password AND your token, they have only seconds before that token is no longer valid anymore.
Two things are special about the tokens. First, the tokens are temporal, meaning they change all the time (usually every 30 seconds or less). If someone steals your password AND your token, they have only seconds before that token is no longer valid anymore.
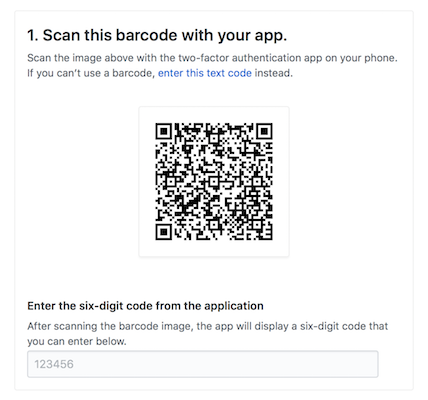 Second, tokens are generated uniquely for you on a separate device that you own and have with you. This device is typically a mobile phone, but can also be a dedicated security key that attaches to your keyring. Even if someone has your password, unless they have access to your token-generating device they cannot log in as you. This makes it significantly more difficult for them to compromise your account.
Second, tokens are generated uniquely for you on a separate device that you own and have with you. This device is typically a mobile phone, but can also be a dedicated security key that attaches to your keyring. Even if someone has your password, unless they have access to your token-generating device they cannot log in as you. This makes it significantly more difficult for them to compromise your account.
How would we know our token?
Tokens are generated with one of the following methods:
- The website sends an SMS text message which is delivered to (presumably) your phone containing the code.
- You set up 2FA within a dedicated mobile app which generates tokens for you, such as Google Authenticator. When you need to get a code, you simply open up the app on your phone to get the current code.
- Many password managers also have the ability to generate the tokens alongside your securely stored passwords. This is similar to setting things up in Google Authenticator, but saves you from launching a separate app by keeping the token generation together with your saved passwords.
- Get a small dedicated security key which only generates tokens, such as an RSA SecurID or YubiKey. When you need a new token, pull it out of your pocket and read off the current numbers.
Note: The most common options involve your mobile phone, making it that much more important to set strong passcodes and screen locks on your devices!
 The most secure option is to get a dedicated security key, but using a Password Manager or Authenticator app on your phone is more than sufficient for most people. SMS should only be used if none of the other options are available, as there have been incidents where attackers have been able to intercept text messages by calling up the phone carrier and redirecting your phone number to their own phone by pretending to be you. Unless you’re a high profile target, you really shouldn’t have to worry much about this, but if you can add a 2nd factor on an app instead of SMS that is preferable.
The most secure option is to get a dedicated security key, but using a Password Manager or Authenticator app on your phone is more than sufficient for most people. SMS should only be used if none of the other options are available, as there have been incidents where attackers have been able to intercept text messages by calling up the phone carrier and redirecting your phone number to their own phone by pretending to be you. Unless you’re a high profile target, you really shouldn’t have to worry much about this, but if you can add a 2nd factor on an app instead of SMS that is preferable.
As we mentioned earlier, unique codes aren’t the only possible second factor. Biometric information such as fingerprints and face scans are becoming increasingly popular as technology makes it easier and less expensive for users. Fingerprint scanners are built-into many computers now, and there are also devices like this YubiKey.

We highly recommend that, at minimum, everyone sets up 2 Factor Authentication on all logins that grant access to sensitive information or anything related to finances. Specifically, all logins to healthcare systems, banks, investment accounts, payroll logins, email, iCloud, Google, website hosting, domain names, credit cards, loans, credit bureaus, bitcoin wallets and other cryptocurrency systems, as well as corporate remote access and VPN logins. Here are some handy guides to get you started:
- Guides for turning on 2FA on a number of common websites: https://www.telesign.com/turnon2fa and https://pixelprivacy.com/resources/two-factor-authentication/
- Using 2FA with the 1Password Password Manager: https://support.1password.com/one-time-passwords/
- Using 2FA with the LastPass Password Manager: https://helpdesk.lastpass.com/multifactor-authentication-options/lastpass-authenticator/
- Setting up 2FA with a Yubikey: https://www.yubico.com/start/
Once you get the hang of it, 2 Factor Authentication is a breeze. Most apps and accounts only prompt you for your 2FA code on a relatively infrequent basis. Generally you’ll always be required to enter it on your first login from a new device, after you haven’t logged in for a number of days, or if you’re logging in from a new physical location that the system doesn’t recognize.
This is just one component of a sound information security strategy. While strong authentication is a critical security control, it alone doesn’t ensure that your sensitive systems and accounts are protected from access by unauthorized users. With our Practical Security Program, we evaluate your risk top-to-bottom by holistically evaluating your environment as an entire system. We help you understand where your risk exposure is, how severe those exposures are, and what investments of time and money make sense as mitigations.
Contact us today for more information about NorthSky Technology and our Practical Security Program!